1.Which statement is true about MAC addresses?
The first three bytes are used by the vendor assigned OUI.
MAC addresses are implemented by software.
The ISO is responsible for MAC addresses regulations.
A NIC only needs a MAC address if connected to a WAN.
2.What is a characteristic of a contention-based access method?
It is a nondeterministic method.
It processes more overhead than the controlled access methods do.
It scales very well under heavy media use.
It has mechanisms to track the turns to access the media.
3.Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
1.Logical link control is implemented in software.
2.The data link layer uses LLC to communicate with the upper layers of the protocol suite.
The LLC sublayer interacts directly with the NIC driver software.
The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
Logical link control is specified in the IEEE 802.3 standard.
4.What is the purpose of the preamble in an Ethernet frame?
is used for timing synchronization
is used to identify the destination address
is used to identify the source address
is used as a padding for data
5.What is the Layer 2 multicast MAC address that corresponds to the Layer 3 IPv4 multicast address 224.139.34.56?
01-00-5E-0B-22-38
FE-80-00-0B-22-38
FF-FF-FF-0B-22-38
00-00-00-0B-22-38
01-5E-00-0B-22-38
6.Which two statements are correct about MAC and IP addresses during data transmission if NAT is not involved? (Choose two.)
1.Destination and source MAC addresses have local significance and change every time a frame goes from one LAN to another.
2.Destination IP addresses in a packet header remain constant along the entire path to a target host.
Destination MAC addresses will never change in a frame that goes across seven routers.
A packet that has crossed four routers has changed the destination IP address four times.
Every time a frame is encapsulated with a new destination MAC address, a new destination IP address is needed.
7.What are two features of ARP? (Choose two.)
1.If a host is ready to send a packet to a local destination device and it has the IP address but not the MAC address of the destination, it generates an ARP broadcast.
2.If a device receiving an ARP request has the destination IPv4 address, it responds with an ARP reply.
An ARP request is sent to all devices on the Ethernet LAN and contains the IP address of the destination host and its multicast MAC address.
When a host is encapsulating a packet into a frame, it refers to the MAC address table to determine the mapping of IP addresses to MAC addresses.
If no device responds to the ARP request, then the originating node will broadcast the data packet to all devices on the network segment.
8.
Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
PC2 will send an ARP reply with its MAC address.
RT1 will send an ARP reply with its Fa0/0 MAC address.
RT1 will send an ARP reply with the PC2 MAC address.
SW1 will send an ARP reply with its Fa0/1 MAC address.
SW1 will send an ARP reply with the PC2 MAC address.
9.A host is trying to send a packet to a device on a remote LAN segment, but there are currently no mappings in its ARP cache. How will the device obtain a destination MAC address?
It will send an ARP request for the MAC address of the default gateway.
It will send a request to the DNS server for the destination MAC address.
It will send an ARP request for the MAC address of the destination device.
It will send the frame and use its own MAC address as the destination.
It will send the frame with a broadcast MAC address.
10.What are two potential network problems that can result from ARP operation? (Choose two.)
1.On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
2.Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
11.A network administrator is connecting two modern switches using a straight-through cable. The switches are new and have never been configured. Which three statements are correct about the final result of the connection? (Choose three.)
1.The link between the switches will work at the fastest speed that is supported by both switches.
2.The link between switches will work as full-duplex.
3.The auto-MDIX feature will configure the interfaces eliminating the need for a crossover cable.
The connection will not be possible unless the administrator changes the cable to a crossover cable.
The duplex capability has to be manually configured because it cannot be negotiated.
If both switches support different speeds, they will each work at their own fastest speed.
12.A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of memory buffering would work best for this task?
shared memory buffering
level 1 cache buffering
fixed configuration buffering
port-based buffering
13.When would a switch record multiple entries for a single switch port in its MAC address table?
when another switch is connected to the switch port
when the switch is configured for Layer 3 switching
when a router is connected to the switch port
when multiple ARP broadcasts have been forwarded
14.
Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
The switch will forward the frame to all ports except port 4.
The switch will forward the frame to all ports.
The switch will forward the frame only to port 2.
The switch will discard the frame.
The switch will forward the frame only to ports 1 and 3.
15.Which two statements describe a fixed configuration Ethernet switch? (Choose two.)
1.A fixed configuration switch may be stackable.
2.The number of ports on the switch cannot be increased.
An SVI cannot be configured on the switch.
The port density of the switch is determined by the Cisco IOS.
The switch cannot be configured with multiple VLANs.
16.How does adding an Ethernet line card affect the form factor of a switch?
By expanding the port density
by increasing the back plane switching speed
by expanding the NVRAM capacity
by making the switch stackable
17.A network administrator issues the following commands on a Layer 3 switch:
DLS1(config)# interface f0/3
DLS1(config-if)# no switchport
DLS1(config-if)# ip address 172.16.0.1 255.255.255.0
DLS1(config-if)# no shutdown
DLS1(config-if)# end
What is the administrator configuring?
A routed port
a Cisco Express Forwarding instance
a trunk interface
a switched virtual interface
18.Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
MAC and IP addresses
MAC address only
MAC and port addresses
port address only
IP address only
19.What statement illustrates a drawback of the CSMA/CD access method?
Collisions can decrease network performance.
Deterministic media access protocols slow network performance.
CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
It is more complex than non-deterministic protocols.
20.Fill in the blank. The binary number 0000 1010 can be expressed as ______ in hexadecimal.
0A
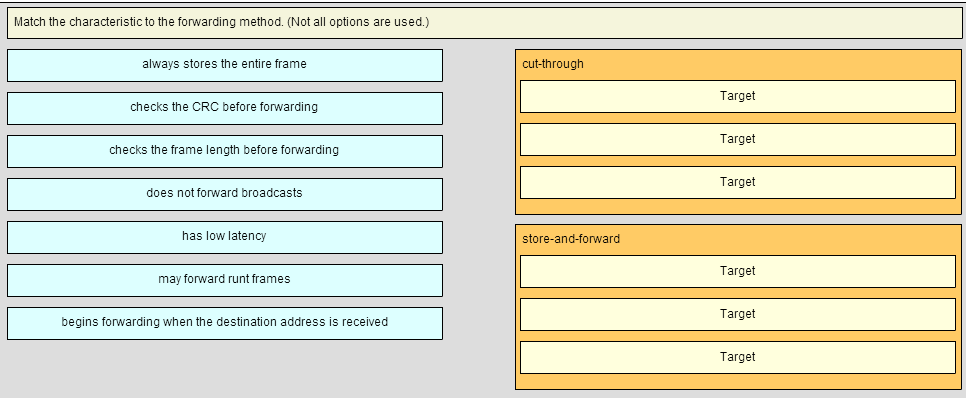
21.Match the characteristic to the forwarding method
A store-and-forward switch always stores the entire frame before forwarding, and checks its CRC and frame length. A cut-through switch can forward frames before receiving the destination address field, thus presenting less latency than a store-and-forward switch. Because the frame can begin to be forwarded before it is completely received, the switch may transmit a corrupt or runt frame. All forwarding methods require a Layer 2 switch to forward broadcast frames.
22.
Open the PT Activity. Perform the tasks in the activity instruction and then answer the question.
What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?
0030.a3e5.0401
00e0.b0be.8014
192.168.0.34
192.168.0.17
0007.ec35.a5c6
23.
24.
Answers:
Beginning of frame- Field 1 = preamble
Field 2 =start frame delimiter
Field 3 =Destination mac address
Field 4 =Source mac address
Field 5 =Length/Type
Field 6 =Encapsulated Data
End of frame-Field 7 =Frame Check Sequence
OTHER version of questions:
1.Why is UDP well suited as the transport layer protocol for video applications?
UDP has low overhead.
2.Which scenario describes a function provided by the transport layer?
A student has two web browser windows open in order to access two web sites. The transport layer ensures the correct web page is delivered to the correct browser window.
3.What is a function of the transport layer?
It segments data from the application layer into manageable pieces.
4.What happens if part of an FTP message is not delivered to the destination?
The part of the FTP message that was lost is re-sent.
5.What type of port number is assigned by IANA to commonly used services and applications?
well-known port
6.Which type of applications are best suited to use UDP as the transport layer protocol?
applications that require minimal transmission delay
7.What protocol header information is used at the transport layer to identify a target application?
port number
8.What is a socket?
the combination of a source IP address and port number or a destination IP address and port number
9.Which two flags in the Layer 4 PDU header are set by a client and server to terminate a TCP conversation? (Choose two.)
FIN
ACK
10.Which transport layer feature is used to guarantee session establishment?
TCP 3-way handshake
11.How does the transport layer provide end-to-end guaranteed data transmission?
TCP retransmits data whenever an ACK flag is not received.
12.Which two flags in the TCP header are used in a TCP three-way handshake to establish connectivity between two network devices? (Choose two.)
ACK
SYN
13.Refer to the exhibit. A TCP segment was sent by PC1 to the web server via port 80. Because of an unexpected network failure, the data was forwarded by R1 but was not received by R2. Which statement is correct about this scenario?
The web server will not acknowledge this segment. The PC1 timer will expire and PC1 will resend the segment.
14.A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the server send before it requires an acknowledgment from the PC?
10 segments
15.A host begins a TCP session with a sequence number of 1000 and sends 10 segments of 1200 bytes each. The last acknowledgement the host receives has an ACK with a sequence number of 7001. What action will the host take next as part of the TCP session?
The host retransmits unacknowledged segments.
16.During a TCP session, a destination device sends an acknowledgment number to the source device. What does the acknowledgment number represent?
the next byte that the destination expects to receive
17.Refer to the exhibit. In the partial Wireshark capture of a packet, which Layer 4 protocol is being used to send data?
UDP
18.How does a client computer determine what source port number to assign to a UDP header?
The port number is random within the range of dynamic port numbers.
19.Fill in the blank.
The layer in the TCP/IP model that links the application layer to the internet layer is called the layer.
transport
Twittear






No hay comentarios:
Publicar un comentario